Great Community of Users Trumps Poor Quality Products
Saturday, June 4th, 2011Every now and then, I run into some weird issue with a software that I truly depend on. What I’m trying to do, looks like a very valid scenario, yet the software just does not want to cooperate. I look at their error message, it is completely misleading. You try to logically reason it out, but you run out of reasons.
Just when you are about to loose hope, you google for the error message and you find a huge number of other users offering solutions. Some problems might be very old know issues, but the folks building the software just never got around to fix them. However, with the help of suggestions from other users, you are able to very quickly solve your issue.
Instantaneously your frustration with the “poor quality” software disappears. You start to love the software even more.
This might sound dramatic, but this is my experience.
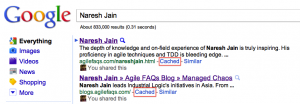
For Example: Recently I noticed that my blog, which runs on wordpress, did not have any description meta-tag.
Asked myself:
Shouldn’t wordpress produce a decent description for each blog post? Guess not!
So I googled for it. Found an easy enough solution. Implemented it. Worked well, except, I started getting the following error on all admin pages:
Warning: Cannot modify header information – headers already sent by (output started at
It says its a Warning, but its a show-stopper. Does not even let me access the admin screens. However people can view my blog just fine.
Again googled for the error message and found a solution. Fixed it. Life is good.
This is the power of having a great community of users. User issues can be fixed in a fairly decentralized way.
Also we all know that “Zero-Defect-Product” is a myth. Any interactive system, can never be fully specified nor fully tested. There will always be scenarios that your team did not think about, but your users are trying to use the product in those scenarios.
So my point is:
Your software might have issues, but sometimes the community can figure out the solution and share it with others, faster than your company can. It does really compensate for not having the highest quality product.
In other words:
You can get away with slightly lower quality product if you are able to build a great community of users around your product.
Of course, if you have a crappy product that does not add any value to any users, then you won’t be able to build a community, no matter how great the quality of your product is.
Also I’ve seen many products that keep everything so closed/secretive, that even if a user wants to help, they simply cannot.
Personally I think those days are gone. This is the era of “more power to the users“ and “more dependence on the users“.